Blog Summary: Hackers are targeting the Graphics card’s VRAM by infecting them with malicious codes. In this blog, you will learn all about the chance revelation of the hacker selling the PoC to the threat actors online.
Nothing is safe anymore, with the progress in technology we all are susceptible to being a victim of cybercrime. No matter if you use the internet on your computer or not, even if you do not use unknown storage devices. This time even a graphics card installed on your computer can cause much damage. With the recent reports, it has come to light that cybercriminals are working on hiding malicious content on your VRAM.
In this blog, find out all about the recent findings of the undetectable malware which can be a part of your graphics card’s VRAM.
Also Read: Fake Call Centers are Spreading Malware through Emails & Free Trials – Microsoft
What happened?
In a recent tweet by a research group – VX-Underground, it was reported that an unknown miscreant has sold a PoC to the hackers. This is said to be incorporated into the VRAM code and likely to be undetectable by the anti-virus programs. This poses a big threat to all PC users as such malware can be the reason behind cybercrimes such as identity theft, online tracking, ransomware etc.
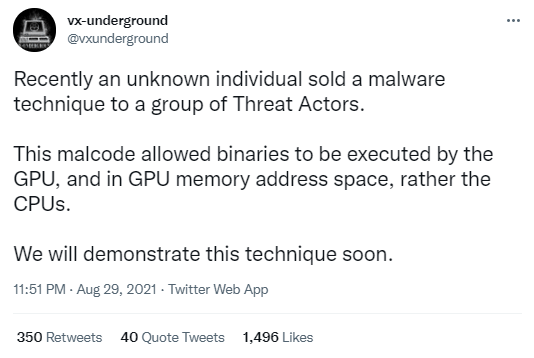
This activity was conducted on a hacker forum and has been said to be talking about the method of infecting the system with the help of VRAM.
Bleeping Computers also said, “Earlier this month, the proof-of-concept (POC) was sold on a hacker forum, potentially marking cybercriminals’ transition to a new sophistication level for their attacks.”
A post appeared on the 8th of August on the hacker’s forum with some information regarding the offer. This is reported that the malicious code has been tested on major graphics card manufacturers. As can be seen from the snapshot above, it can work with Intel, AMD, and NVIDIA GPUs and it is only going to pose a threat to Windows systems. On August 25, it was reportedly sold off as per the same post without much information.
Also Read: Save your Banking Credentials from ‘Vultur’ Malware
What is the potential threat?
Although, this is not a new system as a demo code has been published before they were incomplete or unrefined at that time. This is a new high in cybercrime as it goes deeper and stronger with the new techniques. This is hackers marking a new territory by inflicting the hardware tools. A similar GPU-based malware named Jellyfish was done for Linux six years ago.
But with the introduction of the malware on GPU, the malicious codes go undetected in front of the antivirus, which is the biggest threat. As a user, you might be completely unaware and have potentially harmful malware on your computer. According to the Tweet by VX- underground, the malware code will enable the binaries to execute in the memory of GPU rather than CPU. Mostly, the Windows Defender which is the inbuilt safety guard for Windows PC will help you detect potential threats but this is beyond its limit. This is the main reason why it will remain untraceable by antivirus software for PCs.
Also Read: WhatsApp Mod infects Android Devices With An Impossible-To-Remove Malware.
However, we do not exactly know how this will exploit the PC and the user, it is dangerous to have it mysteriously inhabiting the computer. Another threat is that similar codes for infecting the GPU are available from the 2015 attempts and can be used by other malicious elements to explore this area. I
How can you keep yourself safe?
Even though Windows users are not safe with such threats working on GPUs, one must use anti-virus software on the computer. Choosing antivirus software for your computer is recommended as it will give you protection against the malware which are included in the software. One such software is Systweak Antivirus and we recommend using it as it regularly updates its database and includes the latest computer virus.
Must Read: What Is Pegasus Spyware And How Does It Work?
Wrapping Up-
With the discovery of the codes which infect GPU with the malware, who knows what the cybercriminals can achieve. There is a need for more security features that can help the user in such cases. One needs to implement and work against these researches as they are getting ahead of everyone and it will put all users to danger.
We hope this article will help you learn about the latest hacking techniques used in the hardware. We would like to know your views on this post to make it more useful. Your suggestions and comments are welcome in the comment section below. Share the information with your friends and others by sharing the article on social media.
We love to hear from you!
We are on Facebook and YouTube. For any queries or suggestions, please let us know in the comments section below. We love to get back to you with a solution. We regularly post tips and tricks along with solutions to common issues related to technology.
Related Topics-
Five Smart & Promising Ways To Deter Identity Fraud
What Is Cybersecurity And How To Build A Strategy?
How To Remove Geo-tagging & Other Exif Data From Your Pictures (Phone & PC)?
5 Tech Moguls Caught Misusing User Data
