Cybercriminals have become very active nowadays especially during the Pandemic. This is probably because more and more people are using the PC & the Internet to work, study and meet online with their loved ones. The objective of a hacker is to insert the malware into your system by hook or crook and the modus operandi can be different in all cases. Microsoft cybersecurity researchers have issued a warning to all about a group of malicious actors that spread the BazarLoader malware through fake emails and call centers.
What is BazarLoader?
A BazarLoader malware helps hackers gain backdoor access to an infected Windows host computer. Once the malware is downloaded on your PC, it opens up a backdoor that allows cybercriminals to send other serious malware without being detected and exploit other PCs on the same network. Once the strategy is successful, the hackers scan the environment and can send Ransomware that can encrypt your files and bring your life to stand still. In very simple words, it is something that should not be on your computer
How is BazarLoader Spread?

Many different methods are used by people with malicious intent to spread this malware to your computer. Some of them are by sending attachments through fake emails or sending warning messages through emails which may force the user to call the number provided. Once the user calls the number, the call lands up in a call center where a malicious actor guides the user to navigate to a website, download a file and execute it.
How was this scam identified?
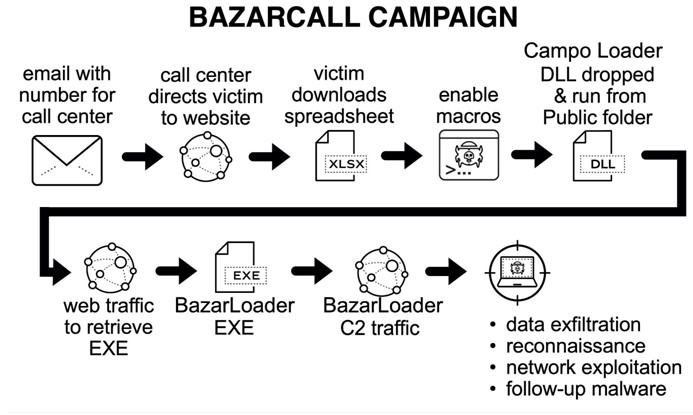
Microsoft CyberSecurity researchers have followed a few cases which led to the same modus operandi used. The call center-based technique is known as BazarCall which is used to take advantage of hundreds of thousands of people who are not very tech-savvy. Microsoft Security Intelligence has announced this on Twitter, warning people to be very cautious and ignore fake emails and scam calls. But the problem here is that “ How do we identify the fake calls and fake emails from the rest?”
The malicious actors have greatly improved their techniques of identifying people to target and are using a variety of different methods to scam people. Microsoft also reported that the attackers were using Cobalt Strike penetration testing kits and this enabled them to get the user’s credentials and Active Directory database.

Earlier, the hackers used to send an infected file through email which is now easily detected by all email service providers and does not allow its users to open such emails. Hence the hackers have retorted to another method which involves sending an email with sensitive content to the user without any infected file. These emails cannot be detected by any email security scanners that are in place today. Microsoft’s Defender and Office 365 apps have cross-domain visibility and are one of the best hopes against this type of attack. Microsoft has also created a GitHub page that provides the latest updates on BazarCall scammers.

How is the BazarCall technique executed?
Here is an example of how this technique is used to infiltrate the PC. This might help you to remain cautious in case you receive such emails or calls.
Note: Make sure to spread this information with all your near and dear ones so that they can be cautious over such scams.
Step 1: A user receives an email stating that some sort of trial subscription that they had subscribed to was going to get expired. Once expired, the subscription will auto-activate and the charges will be levied on their credit card automatically. It also states that they should call the number provided to cancel the subscription and prevent their credit card from getting charged.

Step 2: The user gets terrified due to the unexpected charges that are going to be levied on him/her and calls the number provided.
Step 3: The person who picks up the call may or may not have some sort of information about the user. The user will then be asked for certain personal details like Name, Phone, and Email to begin with.

Step 4: The user will be assured of the issue resolution and directed to a fake website and asked to enter the subscription number provided in the email. This would then download an excel file on the user’s computer.

Step 5: The call center operator will then ask the user to execute the file.

Step 6: The file being an Excel file will open in MS Excel and the user will be asked to enable Macros in the excel and thus run the malware in the system. The Call Center Operator will then state that his/her subscription has now been deactivated and there will be no charge levied on the credit card.
How to prevent malware attacks?
As I mentioned earlier, cybercriminals use ingenious different methods, and hence it is not easy to identify them. Nor do they follow a similar set of steps all the time and this makes it difficult to provide one set of preventive measures that might work in one particular situation but fail in another. The only way is to keep a watch on your credit cards and make sure you do not visit websites that do not follow HTTPS protocol. Constance Vigilance and a knowledge of your monetary affairs and services that you have signed up for are always important.
For example, It does happen when a similar scam is under process when the user realizes during the middle of the call that he never had a credit card, to begin with, so how is he going to be charged? And the call ends abruptly.
Real-Time Antivirus can be a savior
A real-time antivirus is software that scans your PC 24/7 whenever it is switched on and identifies potential threats that may not be updated yet in the virus definitions list. This list is updated frequently by antivirus software organizations and includes the list of the latest virus and malware identified. However, when it comes to identifying malware that is not on the list then you require antivirus software that provides exploit protection. There are a few antiviruses that provide real-time scanning and exploit protection at the same time and one of the trusted ones that we use is Systweak Antivirus.
- Systweak Antivirus provides real-time protection on a 24/7 basis and is always on.
- Facilitates different scan modes as per the needs of the customer.
- Ensures Secure Web Browsing via StopAll Ads extension.
- Helps to delete startup items that slow down the boot time of your computer.
- Improves overall system performance and is a one-stop solution.
The Final Word On Call Centers are Spreading Malware through Fake Emails & Free Trials – Microsoft
Malware has always been a troublesome piece of code for a very long time. And there is no one-stop solution to prevent them from infiltrating them. Once malware is identified by antivirus companies. A new one is developed by malicious actors which are used to scam people until a cure for that new malware is discovered. And the cycle goes on. The only possible way is to install a real-time antivirus app on your computer and remain vigilant about things that you do on your computer. Follow us on social media – Facebook, Instagram and YouTube.



 Subscribe Now & Never Miss The Latest Tech Updates!
Subscribe Now & Never Miss The Latest Tech Updates!