When talking about encryption, most people think of it as only a decade old. However, it is deeply rooted in history. The most famous example can be from the Second World War, when Germans used a machine called Enigma to encrypt the messages before being transferred to their navy.
Traditional data encryption methods were obviously easy to crack by using reverse engineering. But modern encryption techniques are much more complex and require a lot of computing power to crack.
Encryption is mostly used to make information unreadable to anyone trying to intercept the message between sender and receiver.
If anyone other than these two parties want to read the data, it will be in a scrambled or coded form making it unreadable for them. Once decrypted it regains its original form.
In your day-to-day life you encounter several Hyper-networking platforms such as Whatsapp or Online Banking Portals that utilize encryption techniques for secure transmission of data, from one node to another. Though we are familiar with the word but still there is a huge nomenclature associated with encryption standards, which you should be aware of.
So, without wasting any time let’s dive deeper into it!
Encryption Terms Every Computer User Must Know
Plaintext
Plaintext or cleartext is the most basic of the terminologies that is unencrypted and readable by everyone. The data which is left pending for input to encryption algorithms is termed as ‘plaintext’.
Ciphertext

It is the encrypted or illegible data which is the result of encryption algorithm. It is a collection of random numbers and characters, making it useless. ciphertext is sometimes rendered as Cipher but it is more of an algorithm to convert plaintext to ciphertext.
Keys

Cryptographic keys are the means of encryption/decryption of data. It is essential for cryptographic algorithms to understand how plain text will be converted into ciphertext. A key eliminates the need of remembering the entire encryption algorithm, and serves to be an ultimate means of security. The difference between a key and a password is that, a key is algorithm-generated while a password is user-generated.
Hashing
Websites convert the plaintext password to hash using an encryption algorithm and the process is called Hashing. The sender sends the encrypted message as well as the hash to the receiver and the receiver on the other end decrypts the hash as well as the message. Receiver then generates a hash and compare it with the received one. If they appear to be identical, then it accounts for a secure transmission.

Hashing is a faster mode of rendering, since sorting a shortened key value is more efficient rather than using the original value.
Salting
Traditional security methods require additional steps to enhance security. Salting adds a salt which is a random data to the hashed password. The process is called Salting the passwords.
There’s a possibility that people might have same passwords, so to provide more preservation, salting is done.
For example, if two users have same password: Nintendo@91
After hashing, Nintendo@91 is converted into:
f52fbd32b2b3b86ff88ef6c490628285f482af15ddcb29541f94bcf526a3f6c7
But in case, if a hacker attacks the database and reaches this hash, then each account with same hash is equally vulnerable. So, we add a separate salt for each individual to enhance the security.
Example #1: Nintendo@91 + tuna:
3436d420e833d662c480ff64fce63c7d27ddabfb1b6a423f2ea45caa169fb157
Example #2: Nintendo@91 + Raisins:
728963c70b8a570e2501fa618c975509215bd0ff5cddaf405abf06234b20602c
After adding salts to each individual’s password, we can compare the hashes of same passwords With and Without salting-
Without salting:
f52fbd32b2b3b86ff88ef6c490628285f482af15ddcb29541f94bcf526a3f6c7
With salting example #1:
3436d420e833d662c480ff64fce63c7d27ddabfb1b6a423f2ea45caa169fb157
With salting example #2:
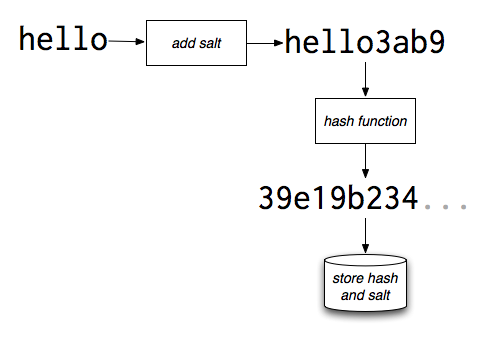
728963c70b8a570e2501fa618c975509215bd0ff5cddaf405abf06234b20602c
Symmetric and Asymmetric Algorithms
Modern encryption algorithm operates on two modes: Symmetric and Asymmetric Algorithms. Symmetric Algorithms uses same key for both encryption and decryption. The key is agreed by both the parties based on mutual understanding. Asymmetric Algorithms uses two different keys: a public key and a private key. This ensures a secure encryption without any need of mutual agreement.
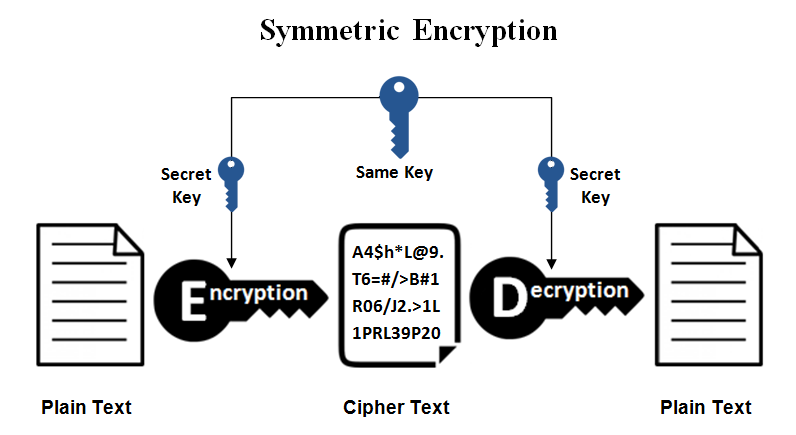

Public and Private Keys
A public key is distributed to everyone in the network but a private key is restricted to a user only. A public key is used to encrypt the message while the recipient needs a private key of the owner to decrypt the message and read the whole content.

Digital Signature
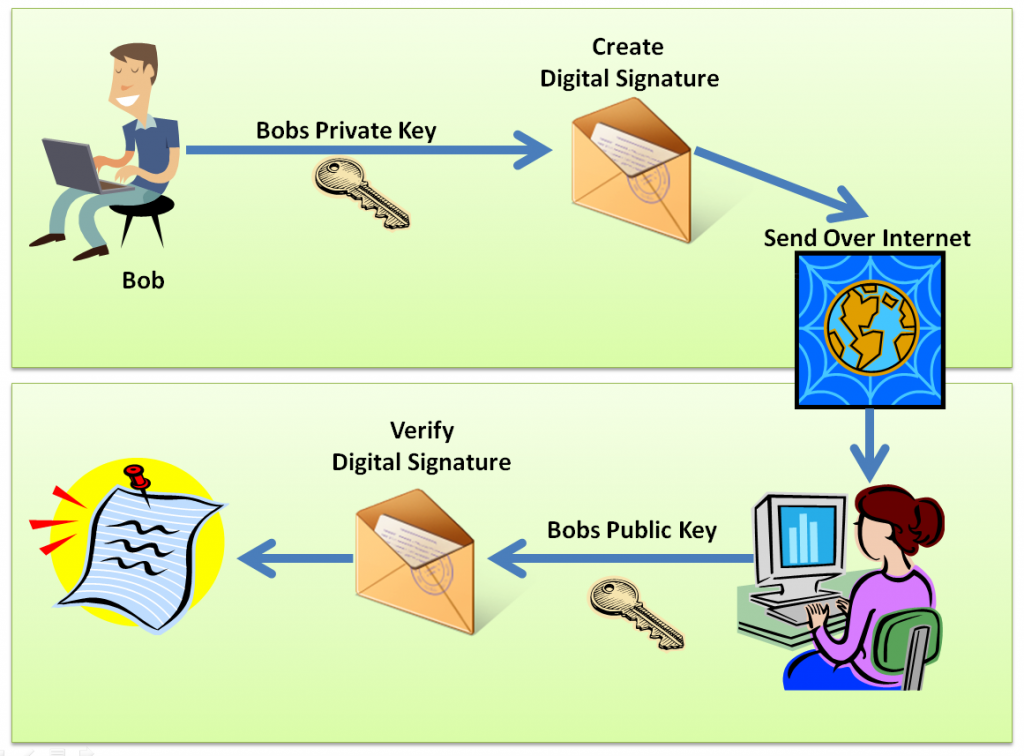
Whenever someone sign a message or a written document, the message is bind with the signatory. Similarly, a digital signature binds the signatory to the digital data. This digital signature can be used to identify the signatory individually by the receiver or any third-party. Signing a hash is more efficient than signing the entire data for faster rendering.
What is Encryption-Decryption Anomaly?
In Encryption, plain text along with encryption key is served as an input to the algorithm to convert the plain text to scrambled or unreadable form. This encrypted message is sent to the receiving party who is able to read the message with a key.
The reverse process is Decryption, the encrypted message or the cipher text received from the sender along with a decryption key is sent as an input to the decryption algorithm to convert the cipher text back to the plain text or readable text.
These encryption and decryption keys are generated by mathematical computations which generates a random number. These keys are valid for a limited time or a session only, after the session end key gets expired.
In Conclusion:
Without encryption, it will be very difficult to carry out most of the vital task we do over the Internet, especially Online transactions. We realis that the mathematical underpinnings attached to encryption is a complicated task for a layman to understand because most of the people are not familiar with the terminologies associated with it. We hope this blog has been a treat for you to grasp the basic encryption terms & its meaning.
Next Read: 5 Best Duplicate File Finder and Remover For Windows 10/11/7 PC


 Subscribe Now & Never Miss The Latest Tech Updates!
Subscribe Now & Never Miss The Latest Tech Updates!