Ransomware continues to dominate the landscape of Cyberspace in from 2017 to 2018. Whether the business is small or big, these attacks have left no stones unturned to make users pay millions of dollars to unlock their own hijacked encrypted files. The explosion of virtual currency like Bitcoin, leave no clues for traceability and has grown pyramid of profitability through digital extortion and made Ransomware a real threat for individuals & business enterprises. According to reports, Individuals are getting attacked every 10 seconds while Businesses are attacked every 40 seconds. Lately, even people with lower technical know are trying their hands at creating copycat ransomware variants to spread terror online.
As this threat is unlikely to subside, let’s look at some highly devastating ransomware attacks that have emerged so far.
Biggest Ransomware Attacks
-
GandCrab
It is the most eminent Ransomware of 2018 and it has spread in huge numbers by now. Apart from the traditional methods of restricting the user to access his own data, GandCrab came up with a fresh technique of doing so. After the processing of malware into your system, it encrypts all the files with a .GDCB extension (for example beach.jpg will be encrypted and renamed to beach.jpg.GDCB) and soon after the encryption process GandCrab generates a decryption file GDCB-DECRYPT.txt, which contains information regarding the current scenario and the instructions for the next step i.e. decryption. In order to decrypt the data, victim needs to visit a TOR browser webpage, acquire the decryption key stored on a remote server handled by the GandCrab’s developers by paying a ransom of about 1.5 Dash(cryptocurrency) which is approximately $300-$500. On successful payment, the decryption key is supposed to be released.

-
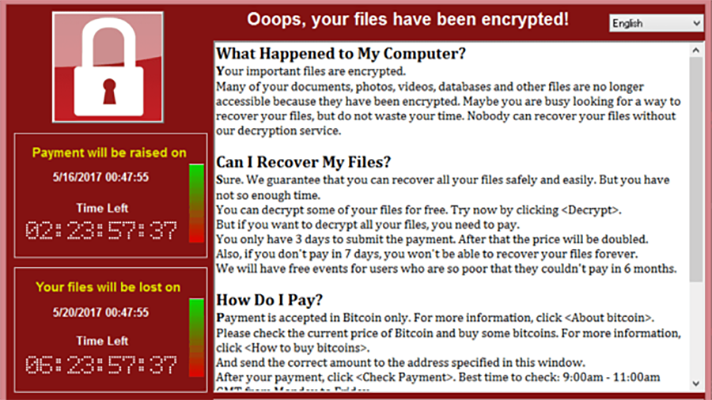
WannaCry
WannaCry is probably the most famous Ransomware attack till date, due to its widespread influence over 150 countries and high-profile targets including Britain’s National Health Service. WannaCry malware enters your system in the form of a ‘dropper’ that consists of several components such, application that encrypts/decrypts files, files consisting encryption keys and a copy of tor browser to make the IP address untraceable. The hackers would ask for a ransom in hundreds of bitcoins to be paid within a limited timeline, creating a sense of urgency by threatening them for loss of data. The initial spread of this RansomWare took place at Microsoft’s SMB (Server Message Block), used to share files between computers typically connected in a closed network but can be exploited if one computer is connected to a public network. Thus, all systems connected to the nodes of SMB became vulnerable to this attack.
-
GoldenEye
Also known as NotPetya, GoldenEye Ransomware attack swarmed across the systems of multi-billion-dollar companies such as FedEx, Merck, Cadbury, AP Moller-Maersk. The combined net worth of these companies is $130 billion, the question that comes to our mind hackers must have asked for more than $300 for every hijacked computer, but the main goal of these hackers was to destroy the data. GoldenEye belongs to the family Petya(thus named NotPetya), which encrypts crucial files on your computer, steal your sensitive credentials and seize your hard drive too. Compared with GoldenEye, WannaCry was fairly basic, GoldenEye not only seizes your data, rather it forces your computer to reboot and simultaneously deletes all logs making it impossible to track down these hackers. The intrusion of the malware behind this Ransomware can be done by someone on your network by tricking you with E-Mail or loaded word document. At last, this malware is the smartest one till date.

-
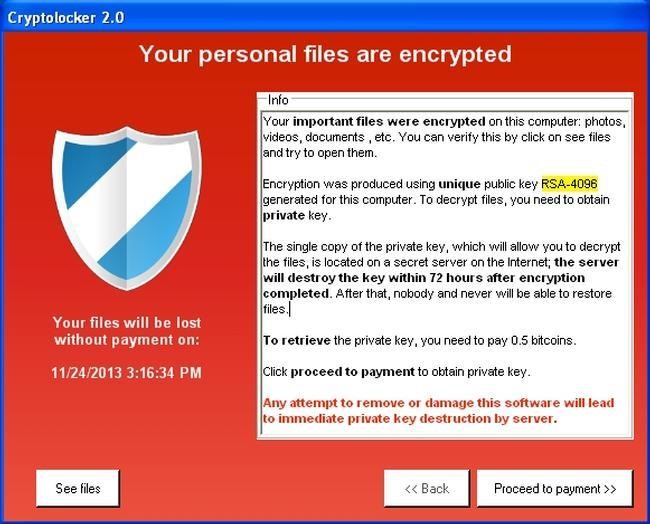
CryptoLocker
Cryptolocker operates on the traditional model of Ransomware, where the invasion of Trojan takes place into your system and eventually encrypting all the vital files on your system and hackers asked for $300 to provide the decryption key required to restore the files. The actual process opted for a social engineering technique which tricks the user to run a password-protected ZIP file which appears to be genuine as an email attachment. When the user opens this file, Trojan automatically runs in the background, generating a symmetric key separately for each file it encrypts. The encryption mode was RSA 2048 bit.
-
zCrypt
zCrypt is kind os ransomware which behaves like viruses. Unlike other ransomware attacks which spreads through emails or downloads, this follows the path of spreading onto different computers via USB sticks. Just after it reaches the target, it generates a file as autorun.inf to execute automatically when the infected USB stick is plugged into a different system. After the attacker encrypts all the data, they ask to make payment within 4 days. After this specific period ransom will increase & then the decryption key stored in hacker’s server will be destroyed if the payment is not made within 7 days. (according to an attack in January 2016).
Major disadvantage with zCrypt is even if the user gives up on his data stole by the attacker, they still cannot use his system. As zCrypt does not stop after it encrypts the existing data, it continues to monitor if any file changes or any new file user has created so that he can encrypt that particular file also. One can only get free after the malware is completely removed.
Must Read: How To Enable Ransomware Protection In Windows Defender?

Apart from all attacks mentioned above, talking about the most recent email attack delivering malicious attachments that contains threat or trojan known as Quant Loader. It is able to install ransomware and password-stealing software. This new attack is breaking two-year-old vulnerability in Internet Explorer that allows the hacker to trespass gateway security features.
But this time attackers have taken another approach by relying on Samba to download files or document, instead of web browser. Therefore, completely bypassing security features. This email is detected to be billing statements and blank emails with just an attachment which contains .zip files. Those zip files contain Windows Script Files (.wsf) which makes Quant Loader to install files but using Samba to install uses file:// instead of an http:// address—it.

What IT Admins Can Do To Keep Their Organization Safe?
Following are some tips for proactively protecting your organization to minimal the risk of ransomware attacks:
- Use Of Two-Step Verification – Phishing campaigns are still very effective these days, it would be a great help for employees to limit the damage. Even in case credentials are lost or stolen, two-step verification can cap the damage to some extent.
- Encrypt All Your Sensitive Data – Every company has encountered even once a data breach issue, encrypting all your crucial information will help in case if it’s stolen, the hacker won’t be able to use it if your data is all encrypted.
- Take Care Of Physical Security As Well – Data can be stolen offline also. It is essential to use surveillance cameras into your organization. So that, no one can enter restricted area and can steal or tamper company’s data.
- Securing The Most Vulnerable Source Of Attack – Emails are the most prone source for ransomware attacks. Most of the time, these attacks are triggered with normal email with infected attachment. Like photos, videos, documents, youtube links or other files which contains malware. Don’t open until & unless you know that mail actually belongs to you or you know the sender in person. In case you got some unknown mail, simply inform your company data security advisor. And delete that mail immediately.
- Make Your Employees Smart – Train your employees about the importance of cybersecurity for you & your organization. And most importantly teach them how to show signs of attacks & react accordingly.
- Be Cautious – Don’t wait for some attack to happen, be vigilant and learn about data breach from law enforcement. Make use of log files & try to identify early signs of attacks or security issues.

Unfolding The Attack?
Following past solutions like saving a clone of all your data on a local backup server is outdated. Though it helps organizations to recover databases quickly in most of the cases, until & unless the problem is not a large site outage. While, currently cloud has an adverse effect on this industry, as it makes very easy if you want to share files between backup server and your main server. You actually don’t have to worry about sharing files through an Internet connection that could be infiltrated. However, Ransomware getting mature with time, has its own way & tactics to corrupt not only your main server but also your backup servers.
Today’s solution for this particular problem is adopting Artificial Intelligence based Machine Learning technology. With the help of ML, developers can train under databases of past ransomware attacks. And then leaving everything on to Machine Learning process that will make connections from those previous attacks to understand & defend against new variants quickly.
From what we’ve seen so far, Ransomware are attacks which are going to increase with time & have greater impact. Organizations will continue to pay amounts to these hackers, instead of taking care of their regular measures like scanning emails, filtering downloads, and updating their systems.


 Subscribe Now & Never Miss The Latest Tech Updates!
Subscribe Now & Never Miss The Latest Tech Updates!