A tale of Cybercrime operation wrought by Microsoft and partners across 35 countries.
To make everything accessible, the Internet connects thousands if not millions of computers, indeed this is great. But when criminal activities grow due to this, things become worse.
Botnet is one such example. It is a network of infected computers capable of infecting other machines and spread malware or malicious software. Once a machine is infected cybercriminals can control it remotely to spread infection.
Most dangerous of all is Necurs – a botnet with the largest networks in the spam email ecosystem with victims in every country.
Knowing this, Microsoft and its partners takedown Necurs and hence becomes the world’s biggest breakthrough in the fight against hackers.
What is Necurs Botnet Malware
Detected in 2012, Necurs botnet is believed to be responsible for 90% of malware spread by email between 2016-2019. Operated from Russia, it is known for distributing GameOver, Trickbot mainly Locky ransomware.
Used as a spambot, this malware spreads either through email attachments or adware. Once on the system, Necurs uses a kernel-mode rootkit to hide and disable security applications like Windows Firewall, etc. Unlike most botnets, Necurs is modular in nature,and it allows operators to change how they operate over time.
What Microsoft and others seize to accomplish?
The OS maker, along with partners across 35 countries – web service suppliers, authorities CERTs, cybersecurity companies, etc. via legal and technical steps, coordinated the takedown of Necurs.

Legal steps covered permission from U.S. District Court to take control of Necurs infrastructure used to distribute malware that could infect over 6 million unique domains in the next 25 months, predicted by Microsoft.
Not only this, but the company is also working with web monitoring service BitSight, internet service providers, computer emergency teams to impose the disrupt. All this is the outcome of an eight-year effort to track Necurs development.
In a 58-day period investigation, Microsoft observed that a Necurs-infected system can send out a total number of 3.8 million spam emails to over 40.6 million possible victims. This made taking down this botnet essential.
To get things in place Microsoft broke down the domain generation algorithm (DGA) technology implemented by Necurs to register new domains and execute attacks.
What is DGA?
It is basically a double-edged sword, a technique that randomly generates domain names at regular intervals, helping malware authors to endlessly switch the location of C&C servers and maintain undisrupted digital communication with the infected machines.

Microsoft reported these domain names to registries around the world and got the domains blocked from becoming a part of Necurs infrastructure.
How Big is Necurs’ Network?
With a network of over 9 million computers, the botnet can conduct various spam attacks like a fake pharmaceutical scam, stock scams, and Russian dating scams. Further, it is capable of launching DDoS attacks and its advanced functions help dodge security mechanisms placed in the organizations.
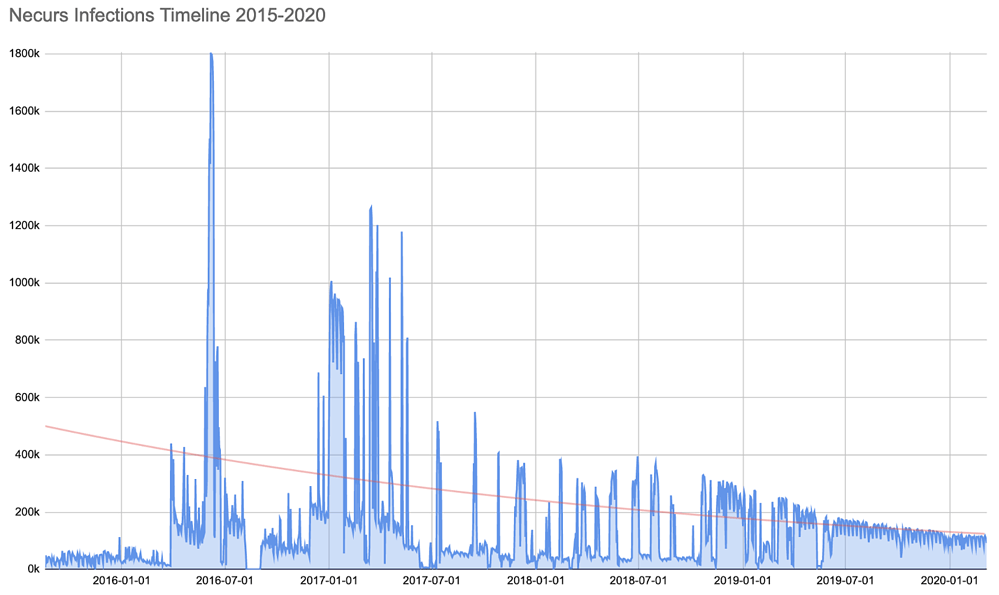
Attackers use this network of bots to distribute malware like GameOver Zeus Dridex, Locky, Trickbot), sending spam emails, cryptomining, identity theft, romance, and financial scams.
Is Necurs Dead? Or Being Replaced?
Certainly, Microsoft disrupted Necurs – a botnet capable of sending malicious emails by ditching spam filters. But this doesn’t mean there will be no more targeted attacks. Cybercriminals are now watching Emotet malware and considering it as a replacement of Necurs.
If that is true approximately 2 million systems will be infected by Emotet – a malware that stays on an infected system capable of reading emails content and inserting itself into ongoing conversations between trusted partied within the organization.
This means more trojan attacks. The only way to stay protected is to keep a check on all the activities you do online. With this, we hope that companies, researcher keeps on hunting more such infections and clear them to let us stay safe.
If you think we can do something else do share your thoughts and let us know what can be done. Your thoughts and feedbacks are valuable, so do share.


 Subscribe Now & Never Miss The Latest Tech Updates!
Subscribe Now & Never Miss The Latest Tech Updates!